
A Simplified Guide to Understanding JSON Web Tokens (JWT)
Empowering Web Security: The Dominance of JWT Authentication in Modern Applications
I. Introduction:
JSON Web Tokens (JWT) has emerged as a versatile and widely adopted method for securely transmitting information between client and server. This article delves into the intricacies of JWT, exploring its components, advantages, and practical applications in web development.
II. Understanding JWT
A. Components of JWT
Header:
Think of the header as the packaging of a parcel. It contains information about how the parcel (JWT) should be handled.
The header typically consists of two parts: the type of the token, which is JWT, and the signing algorithm being used, such as HMAC SHA256 or RSA.
For example:

Payload:
The payload is the actual content of the parcel. It holds the information you want to share.
The payload in a JWT contains "claims," which are statements about a user and additional data.
Claims fall into three categories: registered, public, and private claims.
Types of Claims:
Registered Claims: Predefined and recommended claims like issuer (iss), expiration time (exp), subject (sub), and audience (aud).
Public Claims: User-defined claims, but to avoid issues, they should be registered in the JSON Web Token Registry or use a collision-resistant namespace in a URI.
Private Claims: Custom claims for sharing information between parties that agree on using them.
Compact Design:
Claim names are intentionally kept short (three characters) to maintain JWT's compact nature.
For Example:

The payload is then Base64Url encoded to form the second part of the JSON Web Token.
Signature:
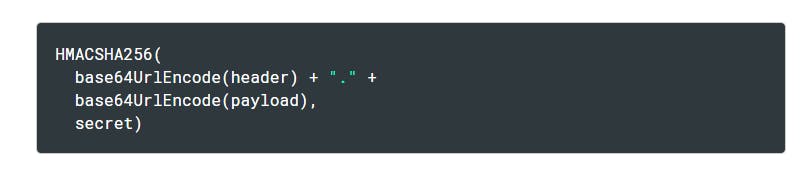
The signature is like the seal on the package. It ensures that the contents haven't been tampered with during delivery.
To create the signature part you have to take the encoded header, the encoded payload, a secret, the algorithm specified in the header, and sign that.
For example:
B. How JWT Works in the Context of Authentication
- JWT is like a digital passport for your online activities. When you log in, the server gives you this passport (JWT), which contains details about you (like your username). You show this passport whenever you want to access certain areas (authenticate).
Understanding JWT becomes like understanding the parts of a letter – the envelope (header), the letter inside (payload), and the wax seal (signature). It's this simple yet secure way of sharing information on the internet.
Putting it all together
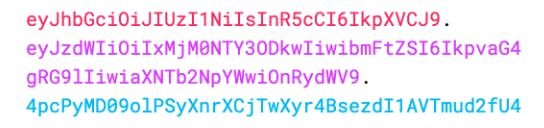
JWT produces three Base64-URL strings, separated by dots. These strings are easily transferable in HTML and HTTP settings.
This format is more efficient and concise compared to XML-based standards like SAML
The output comprises a series of three strings (header, payload, and signature), making it easy to work with in web environments.
This simplicity enhances its usability in transmitting data through HTML and HTTP.
A demonstration of a JWT includes a header and payload that are encoded and then signed using a secret.
This showcases how JWT combines data (header and payload) and ensures its integrity through a signature, providing a secure and streamlined data exchange mechanism.
If you want to play with JWT and put these concepts into practice, you can use jwt.io Debugger to decode, verify, and generate JWTs.
Feel free to explore this GitHub repository for insights into how JWT is implemented in a Node.js environment.
Conclusion
JWT emerges as a powerful and secure means of transmitting information in web development, with a compact design, clear components, and versatile applications in authentication and data exchange.
